"Demystifying the OSI Model: The Backbone of Modern Networking"
Concept
The Open Systems Interconnection model (OSI model) is a framework to describe the seven (or more) abstraction layers on which communication between devices occurs. These layers, from bottom to top, are as follows:
- Physical
- Data Link
- Network
- Transport
- Session
- Presentation
- Application
Each layer serves a specific purpose within a greater systematic approach to networking and network security. Each layer builds on the layer before it, so order matters! In the field of Information Technology, the OSI model is useful in identifying threats and troubleshooting device and network issues. It provides a categorical approach to identifying and addressing vulnerabilities or malfunctions. It also helps in understanding where a business should be putting the most emphasis on security. For example, if the business primarily stores data on the cloud, its highest security would be on a different layer than a business that stores most of its data locally.
In-depth Analysis 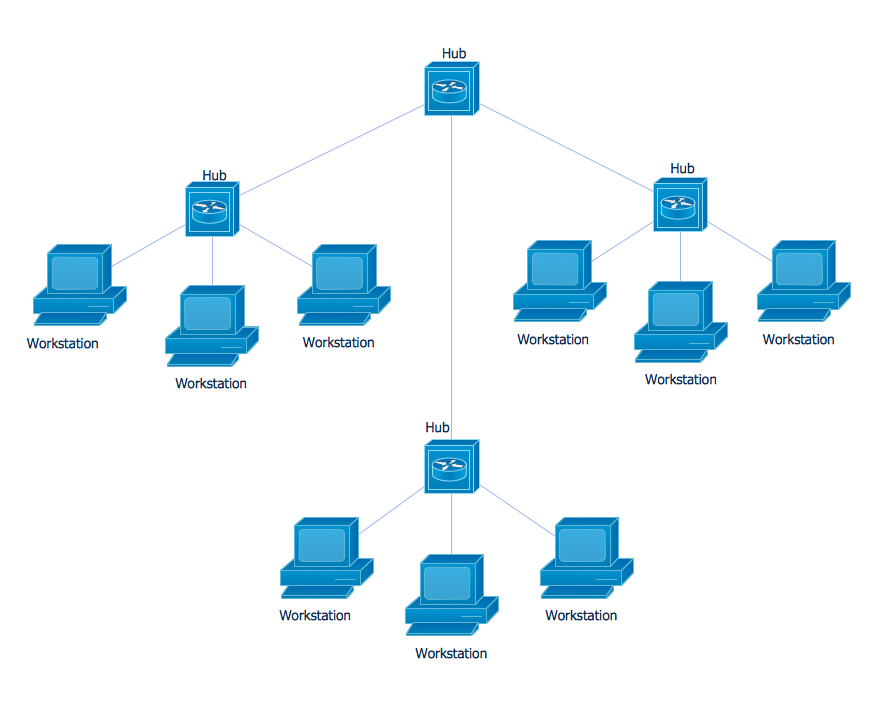
[1] Physical layer
As the name suggests, this layer is made up of the physical and electronic link between two devices. This includes wireless frequency links, such as Wi-Fi, or physical network components such as an Ethernet hub and cabling. Data traveling through a physical medium is raw data, known as bits, made up of 1s and 0s. Computers sharing a network can be connected using a variety of topologies. This figure shows a star topology, which is the most common type of network topology!
Functions:
This layer is in charge of syncing the bits for the sender and receiver using an internal clock, as well as managing the bit rate of data transfer. The physical layer also establishes cable topologies, which are different systems of connecting network devices.
Vulnerabilities and Exploits:
One threat to physical security that people often overlook is danger from natural factors. If the physical components of a network are not protected from the elements (such as flooding or an earthquake), it would be considered a denial of service (DoS) attack. For instance, if a business is operating in an area prone to flooding, it should make sure to keep those components elevated. Another threat is the potential of human vandalism, such as cutting wires.
Security:
One way to protect a layer of a network is to have backups. On the physical layer, this would look like having multiple circuits handling the internet connection. Another option is to keep core network elements and storage in a cloud data center, to allow a switch to wireless if the physical components are unserviceable.
一 * 一
[2] Data Link Layer (DLL)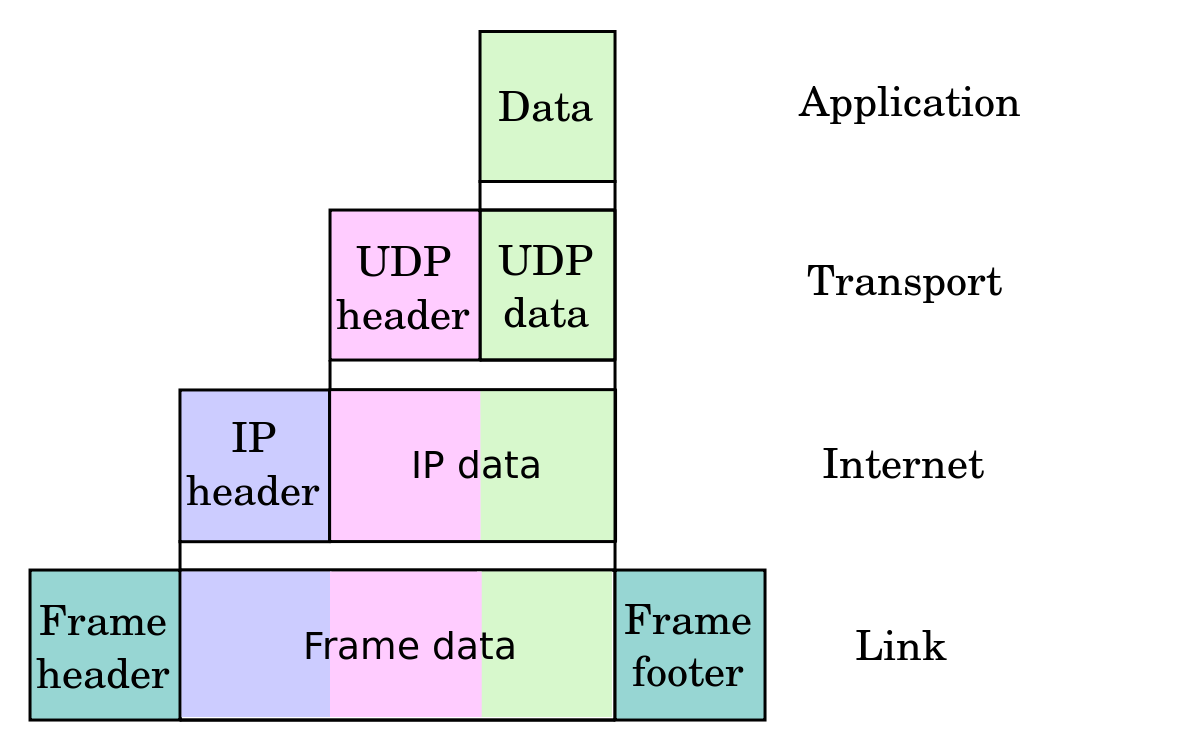
Once a message has been sent to the physical layer, it is the job of the data link layer to ensure that a message makes it from one node to another, and then to the correct destination. Any device connected to a network can act as a physical network node. Messages that are sent jump through these nodes to make it to their destination. The DLL uses MAC addresses to address a message to the correct host. It is important to note that this layer is tied to the physical layer. MAC addresses are only local identifiers, and data being sent to another network will be directed using the network layer.
Functions:
The data link layer is in charge of a process called framing. In networking, the term “frame” is a unit of data that a sent message is divided into for efficiency and security. This layer is also in charge of assigning MAC addresses to the header of each sent frame. MAC addresses are unique identifiers of devices on a network. Then, once the correct sender and receiver are identified, the DLL manages any errors that occur when sending frames as well as controlling the consistency of the data that is sent and received.
Vulnerabilities and Exploits:
The data link layer is susceptible to attacks on the Local Area Network. At a smaller level, frames can be subject to sniffing, and spoofing. Sniffing is the act of maliciously monitoring and capturing sent data. Spoofing is an attack based on deception by falsifying something illegitimate as legitimate.
- One attack on this layer is called MAC Flooding, an attack that targets and overloads network switches (devices in charge of connections between devices). The attack is meant to leak user data or cause a DoS attack by forcing the switch to send out all frames to all ports, rather than just its intended destination.
- Another vulnerability concerning the network switch is called port stealing. Port stealing is when an attacker steals a victim’s MAC address, and causes the switch to send data to the stolen address rather than the authentic one. This is a man-in-the-middle attack, where a user intercepts data between a sender and a receiver. From their vantage point, an attacker can read all the information sent to the user, cause delays, and stop the victim from receiving information.
- A third existing vulnerability on this layer is a network protocol called the Address Resolution Protocol (ARP). Network protocols are a universal language for communication between different devices. Each protocol has a set of rules that regulates communications and/or data processing across networks. The ARP is in charge of translating between MAC addresses (local identifiers) and IP addresses (global identifiers), but this protocol can be intercepted by a malicious packet that leads to a user being able to see all packets sent and received within a network. This is another example of a man-in-the-middle attack. A second vulnerable network protocol is Dynamic Host Configuration Protocol (DHCP). This protocol can be exploited to overload a server or spoofed to deny access to authenticated users.
Security:
Improving port security is an effective way of protecting against attacks on the data link layer. Imposing authentication by tying a physical port of a switch to a specific MAC address or addresses can secure a network by eliminating available switch ports to connect to. In addition, monitoring and logging network events can provide security by having event traceability and alerting administrators of any suspicious activity.
一 * 一
[3] Network layer
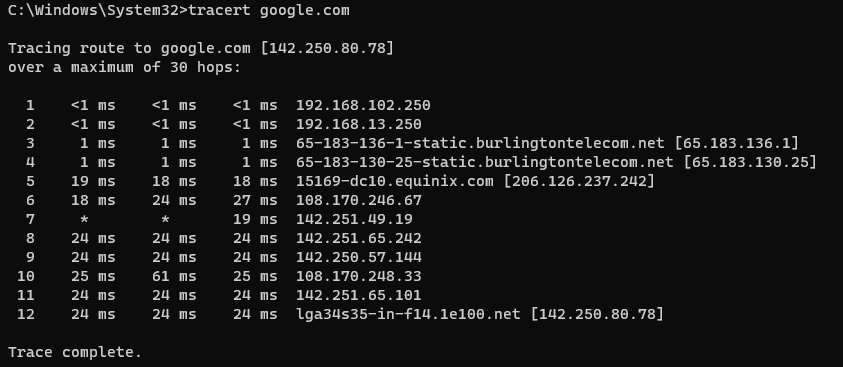
While the data link layer is more focused on local, physical connections, the network layer is responsible for transmitting data to hosts on different networks. This layer is in charge of finding routes for data to follow, just like how data would jump from node to node on the data link layer. You can observe how a message follows a path of nodes by using the “tracert” command in the command prompt, just type in “tracert google.com”, or replace google.com with any other web address or IP address.
Functions:
Packets are segments of data within the network layer just as frames are segments of data within the data link layer. When data needs to be sent outside of a network, it becomes a packet. Packet transmission has a large number of options for routes to take. The network layer chooses the best route for data transmission to take. This involves uniquely identifying networks globally with IP addresses. This is called logical addressing. These addresses are included in the headers of sent packets.
Vulnerabilities and Exploits:
Unlike the previous two layers, attacks on the network layer can come from the internet. Often, threat actors will target a network’s router, including attacks like sniffing, spoofing, and DoS.
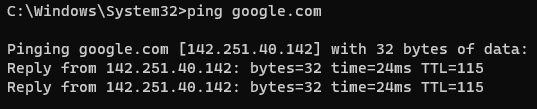
- An ICMP flood is a distributed denial of service attack that is executed by overwhelming a network device (usually a router) with continuous request packets known as pings. The device attempts to respond to all the requests but is unable to keep up with the volume of traffic it is receiving, This causes freezing or crashing, and users are unable to connect to the network. You can “ping” a network by typing the command “ping google.com” into the command prompt or replacing google.com with any other web address or IP address.
- A wormhole attack is an exploit that detects a compromised network node and directs packets from the compromised (hacked) node to a malicious one. Two illegitimate nodes are placed within a network to create a short path between the nodes for packets to follow. This attack is a man-in-the-middle attack, where the attacker(s) can listen in on transmissions between the two nodes by packet sniffing. These paths can also cause complications with routing algorithms, as well as issues with the packets themselves.
- A related attack is a sinkhole attack. A compromised or malicious node becomes a sinkhole by luring in traffic from all surrounding nodes. The sinkhole is capable of altering data within packets that pass through the node, thereby compromising network security.
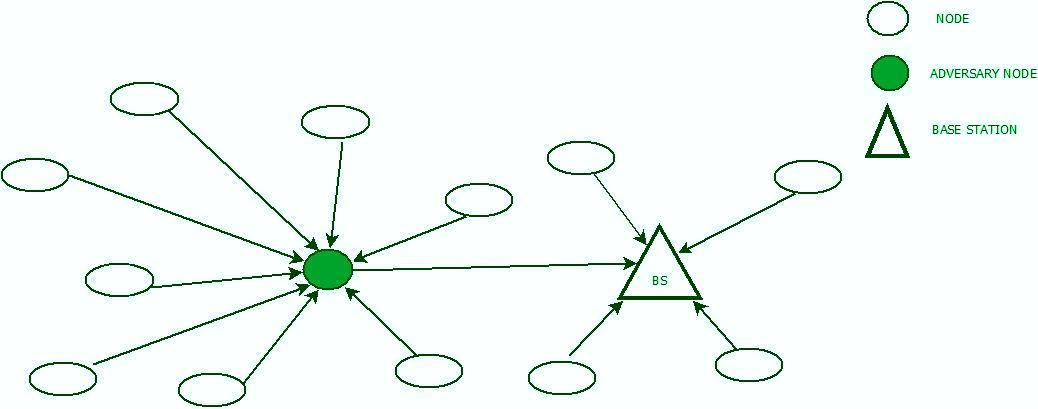
Security:
Security on the network layer can be implemented by utilizing Access Control Lists to allow administrators to view all devices that can access the network, authentication protocols to verify devices, configuring firewalls to segment the network and control access, and monitoring systems to identify suspicious network activity. Routers, firewalls, and switch configurations should be monitored and up to date. All traffic on the network switch should be encrypted.
一 * 一
[4] Transport layer
The transport layer uses services from the network layer and provides services to the application layer. The term “end to end” is used in this layer to encapsulate the entire transportation process from the sender to the receiver. If a message was not sent “end to end”, this layer is also responsible for communicating an error and re-transmission if possible.
Functions:
The transport layer incorporates source and destination port numbers in the headers of its data, which is separated into units called segments. Once reaching the destination, the segments are reassembled to present the data in its original form. This layer can establish a connection in a way that relays an acknowledgment back to the sender of a message to make transmissions reliable and secure. However, this type of communication is slower, and disregarding the acknowledgment process allows for much faster data transmission.
Vulnerabilities and Exploits:
One of the biggest vulnerabilities of the transport layer is open or unsecured ports. Ports in the context of networking are virtual network points that are associated with specific processes and services for communication purposes. A technique known as fingerprinting can be used to discover vulnerable ports within a target system.
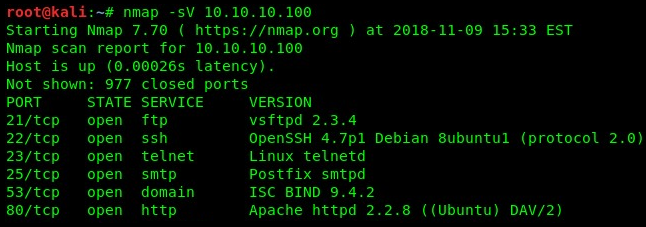
- Enumeration techniques can then be executed on vulnerable ports to extract information. One example of an exploitable port is port 25: Simple Mail Transfer Protocol (SMTP). This protocol is used in mail servers to send mail out to other users. It includes commands for identifying valid users on a system, which could allow a hacker access to this information if they gain access to the system using the vulnerable port.
- A SYN flood attack describes a DoS attack in which an attacker takes advantage of a mechanism called a TCP 3-way handshake. This handshake is in charge of establishing a secure connection (as described in the “functions” section). When packets are sent to a destination, they are sent as “TCP SYN” to indicate that it is looking to synchronize with the device. Then, an acknowledgment packet called a “TCP ACK” must be sent back in response. Knowing that this system is in place, a hacker can send an influx of TCP SYN packets to a target system to overwhelm it and cause it to abruptly stop responding to valid incoming requests.
Security:
A protocol known as Transport Layer Security (TLS) works on layers 4-7 of the OSI layer to encrypt and protect internet communications end-to-end. It is a standard protocol to employ that can prevent eavesdropping and data tampering on applications such as web browsers, instant messaging, and mail services.
一 * 一
[5] Session layer
In short, the session layer coordinates aspects of communication sessions between devices. Sessions are used to define a sequence of interactions between two communicating systems. After the transport layer establishes a connection between two devices, this layer can maintain these connections. It is in charge of creating or terminating sessions, as well as integrating functions such as user authentication. Session tokens are unique identifiers assigned to specific session instances to authenticate requests made between the connected systems and maintain continuity.
Functions:
Synchronization points in the session layer act as checkpoints within streams of data that can be referred back to when a communication failure occurs. The session layer establishes protocols for checkpointing that dictate when a session should be resumed, restarted, or terminated. Systems can communicate in half-duplex mode (one direction; has one sender and one receiver) or full-duplex mode (two-way communication), which is defined on this layer. The session layer commonly implements its services in applications using remote procedure call (RPC) protocols. RPC is used to allow a user’s machine to work with processes on remote systems as if they were working directly (locally) on those systems. An example of this would be accessing files or databases within a server from a home computer.
Vulnerabilities and Exploits:
Session hijacking refers to the end goal of an attack that targets a user’s web session by obtaining, intercepting, or manipulating a session token. Session tokens are highly valuable, as anyone who obtains the token could impersonate a legitimate user. A compromised user could have their browsing session infiltrated and can gain access to confidential information within that session such as banking information or passwords.
- Cross-site scripting (XSS) is a type of injection attack, which is an exploit performed by a hacker by inserting malicious code into an existing computer program and changing its execution. For example, an attacker can alter the link within an otherwise trustworthy (but vulnerable) website to lead to a harmful website. In the session layer, XSS can be performed as a way to compromise a session token.
Security:
HyperText Transfer Protocol Secure (HTTPS) should be implemented on websites to ensure encryption. It is the primary protocol that is used to send data between browsers and websites. Websites using HTTPS have a lock next to the URL that can be clicked to view details about its SSL certificate, which authorizes websites as using HTTPS and therefore secure. Users accessing HTTP websites should be aware that there is a security risk involved. Vulnerability to XSS comes from unsecured code within a website or application. Constantly updating programs ensures that the most secure version of a service is being used, minimizing the risk of any potential flaws being taken advantage of.
一 * 一
[6] Presentation Layer
Often, when considering the OSI model, the top three layers (session, presentation, and application) are grouped together as they work concurrently in the transmission process to provide an interface on either end of the communication. As such, the lines between these layers are blurred. For example, the HTTP protocol mentioned as part of the session layer has aspects of the presentation layer while generally being considered as part of the application layer. Using HTTP, the presentation layer’s job would be to identify encoding for translation purposes. Otherwise, this layer plays a part in transforming complex application data into compressed data for transmission, or vice versa (as the OSI model works both ways).
Functions:
The presentation layer’s primary function is to translate data into a usable form between the application and the network layer. This includes data encryption and decryption, compressing data to reduce the amount of data being transmitted, and converting data into the appropriate format according to its corresponding application (e.g. Is this an email? A request to load a webpage? A file transfer?).
Vulnerabilities and Exploits:
With encryption happening on this layer, hackers may try to brute-force or otherwise crack the implemented encryption in various ways. By targeting flaws in encryption protocols such as SSL, hackers may be able to intercept the data. SSL hijacking is done by generating a fake certificate for a website that a user is visiting, trying to make them believe a website is secure when it is malicious.
- Phishing, the practice of trying to trick users into installing malware revealing personal information by pretending to be a credible person or organization, can also be executed on this layer. Cross-site request forgery is the term for describing an attack that occurs within an application that attempts to force users into carrying out unwanted, malicious actions.
Security:
Often, SSL attacks will go undetected because inspecting the encryption packets is an intensive process. Ensuring that a secure system for encryption is in place could prevent this from becoming an issue. Otherwise, inspecting application traffic for suspicious activity or policy violations is useful for detecting potential attacks. A program like an application delivery platform can handle application security and monitoring as well as add an extra layer of protection. When aiming to prevent social engineering attacks such as phishing, it is important to train all employees and users to recognize and report potential scams. Additionally, having a plan for what to do in case of a disaster is vital for harm reduction as it is impossible to be 100% secure.
一 * 一
[7] Application layer:
On either end of a communication, the application layer is the window between the application interface that a user interacts with and the network. When an application generates data to be sent across a network, this layer provides protocols for the software to be able to meaningfully send and receive the data. It defines the interface methods that a host (one’s own computer or other device) uses when communicating.
Functions:
Once a communication has occurred, the application layer displays the received data to the user. An additional function of this layer includes the use of a network virtual terminal to connect a user to a remote host (in other words, being able to access a computer through another, distant computer), and the ability to use File Transfer Access and Management (FTAM) to access, receive, manage, or control authorized files from a remote computer.
Vulnerabilities and Exploits:
There are a plethora of exploits that exist on the application layer, because every software may have its security flaws, and therefore is the most difficult to secure. Many hackers seek to take advantage of weak code within an application or software, and eventually attempt to gain as many privileges as possible using vertical privilege escalation. A lot of the terms used to refer to different types of exploits target this layer, such as viruses, worms, keyloggers, backdoors, and trojan horses.
- An attack similar to a DDoS attack that occurs on this layer uses a program called Slowloris. Slowloris targets a web server (HTTP connections) and takes it down by overloading it with as many connections as possible without completing any requests. This way, each connection starts a session that is reserved a “slot”, and eventually the web server cannot handle any more requests. It’s an effective way to target certain web servers that do not require a lot of data transmission. What makes Slowloris unique is its slow and hard-to-detect attacks that may appear as regular traffic before the server is flooded.
- A trojan horse describes a social engineering attack in which a program or application is disguised as legitimate to trick users into downloading it, unaware that it is malware. The malware usually gives a hacker access to the network, in which they can export, modify, or delete files. Though, “trojan horse attack” is a broad term the end goal of the hacker behind the malware could be a variety of things.
Security:
- Monitoring applications is an effective way to identify and address application layer threats. This layer has the highest risk of zero-day attacks, which are undetected attacks that target unknown security vulnerabilities. With proper implementation of algorithms, technologies, and approaches to tracking and managing attacks, the risk and impact of attacks including zero-day attacks can be minimized.
- Proper forms of authorization should also be present within applications. Web application firewalls can monitor and filter traffic to web applications to protect against injection attacks. Implementing a secure web gateway increases security within a network by enforcing corporate policies on the types of applications that are accessible, and blocking the use or download of any possibly malicious software or websites.
Works Cited
https://en.wikipedia.org/wiki/OSI_model
https://www.geeksforgeeks.org/open-systems-interconnection-model-osi/
https://www.splunk.com/en_us/blog/learn/osi-model.html
https://gofortress.com/osi-model-7-layers-of-security/
https://training.nhlearninggroup.com/blog/7-layers-of-cybersecurity-threats-in-the-iso-osi-model
https://www.csun.edu/ansr/classes/comp424/project/attacks/2.pdf
https://hub.packtpub.com/vulnerabilities-in-the-application-and-transport-layer-
https://securityintelligence.com/articles/osi-model-stopping-threats-session-layer/
https://www.checkpoint.com/cyber-hub/network-security/what-is-secure-web-gateway/
