March 23, 2023
Author: Cameron Jalbert
What is Vishing?
Vishing, short for “voice phishing,” is a type of social engineering attack that involves using phone calls or voice messages to trick victims into sharing their sensitive information. An attacker may be seeking information such as credit card numbers, social security numbers, or login credentials.

Vishing vs. Phishing
While vishing and phishing are both social engineering tactics, they differ in execution. Phishing usually involves using email or other digital communication channels, while vishing involves using phone calls or voice messages. Both tactics rely on playing on human vulnerabilities such as trust, fear, and urgency.
How Does Vishing Work?
Vishers (cybercriminals who use vishing) use a variety of tactics to make their calls seem legitimate and trustworthy. They may pose as representatives from banks, government agencies, or other organizations. Vishers may also use techniques such as spoofing, where they manipulate the caller ID to make it appear as though the call is coming from a legitimate organization. They may also use pre-recorded messages or interactive voice response systems to make the call seem more authentic.
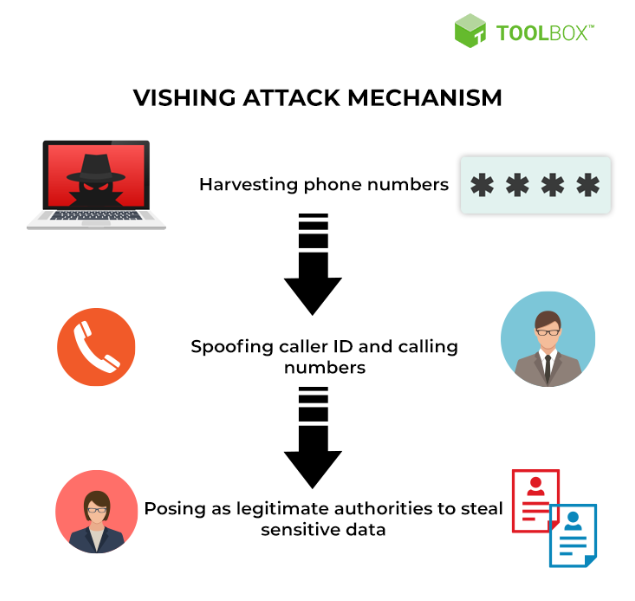
Source: spiceworks.com
Example of Vishing
The following video is about Jessica Clark, a social-engineering hacker who was given permission to try and gain access to someone else’s bank account. Feel free to watch the short 2-minute video below to see how fast she does it:
https://www.youtube.com/watch?v=lc7scxvKQOo
Why is Vishing Effective?
Vishing can be highly effective because it plays on human vulnerabilities such as trust, fear, and urgency. Vishers often use sophisticated techniques to make their calls seem legitimate and trustworthy. In just 2021 alone, over 59.4 million Americans lost 29.8 Billion dollars to vishing. It’s important to remember that 85 percent of attacks are used with a smartphone which nearly all of us have.
How Can You Protect Yourself from Vishing?
There are several steps you can take to protect yourself from vishing attacks:
- Being skeptical of unsolicited calls or messages, especially the ones that ask for sensitive information.
- Verify the identity of the caller or message sender before providing any information. Call the organization back using a verified phone number or visit their website directly.
- Avoid providing sensitive information over the phone or through voice messages.
- Use strong, unique passwords and enable two-factor authentication whenever possible.
- Educate yourself on the latest vishing tactics and stay informed about common scams.
The Role of Technology in Preventing Vishing
Technology can play an important role in preventing vishing attacks. Some strategies that organizations can use to protect themselves and their customers include implementing two-factor authentication, using anti-spoofing technology, providing both customer and employee education, and monitoring for suspicious activity. 2FA would allow for verification of who is on the other end of the line. Anti-spoofing tech would prevent vishers from being able to impersonate legitimate organizations’ phone numbers.
Legal Consequences & Conclusion
Vishing is illegal in most jurisdictions and is considered a form of fraud. In addition to criminal penalties, victims of vishing may be able to pursue civil legal action against the perpetrator.
Vishing is a serious threat that can result in great financial loss, loss of secure access control, and other negative consequences for victims. By staying informed about the latest vishing tactics and taking steps to protect yourself and your organization, you can reduce the risk of falling victim to these types of attacks. Remember, always be skeptical of unsolicited calls or messages, verify the identity of the caller, and avoid providing sensitive information over the phone or through voice messages. By working together to combat vishing, we can help keep ourselves and our communities safe from fraud and other types of cybercrime.
Resources:
- University, Carnegie Mellon. Social Engineering – Information Security Office – Computing Services – Carnegie Mellon University, https://www.cmu.edu/iso/aware/dont-take-the-bait/social-engineering.html
- Dupaul, Neil. “Hacking the Mind: How & Why Social Engineering Works.” Veracode, 2013, https://www.veracode.com/blog/2013/03/hacking-the-mind-how-why-social-engineering-works
- Swanagan, Michael, et al. “What Is a Vishing Attack?” PurpleSec, 24 Oct. 2022, https://purplesec.us/vishing-attacks/
- Cooke, Trevor. “Vishing Statistics 2023: Costs of Voice Phishing Attacks.” EarthWeb, 12 Mar. 2023, https://earthweb.com/vishing-statistics/
- BasuMallick, Chiradeep. “What Is Vishing? Definition, Methods, and Prevention Best Practices for 2022.” Spiceworks, 27 July 2022, https://www.spiceworks.com/it-security/cyber-risk-management/articles/what-is-vishing/
- Mind, Oracle. This Is How Hackers Hack You Using Simple Social Engineering . YouTube, YouTube, 1 May 2016, https://www.youtube.com/watch?v=lc7scxvKQOo Accessed 20 Mar. 2023.
