Do you usually trust the websites you browse based on how they look? Facebook, Amazon, and Google – they all have a distinct look that you can recognize right away! What would happen if the link you clicked on led to a more malicious, yet familiar, site?
November 30, 2021
Author: Eric Burdick
What is the Social Engineer Toolkit?
The Social Engineering Toolkit was invented by the founder of TrustedSec, Dave Kennedy. The tool was created to test and check for vulnerabilities within a network. The testing area consists of the users connected to it, as well as the entire network infrastructure. While the purpose of this tool is only supposed to be for good, some use the toolkit to gain and extract information from unsuspecting users.
How does the toolkit work?
The kit can be installed from the TrustedSec website and is compatible with Windows, Linux, and Unix, and runs off of the command prompt. After accepting the agreement, the options will guide you to different methods of attack to test against a network. For this article, we will talk about website attack vectors.
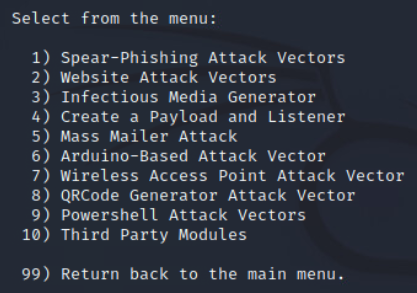
SET Options
Creating a fake website
Through a few selections, we are given the option to use the provided templates for websites, in which Google is chosen. From there a link will be created. Anybody who searches this URL will be led to a Google sign-on screen. But is it Google? See if you can notice any differences.
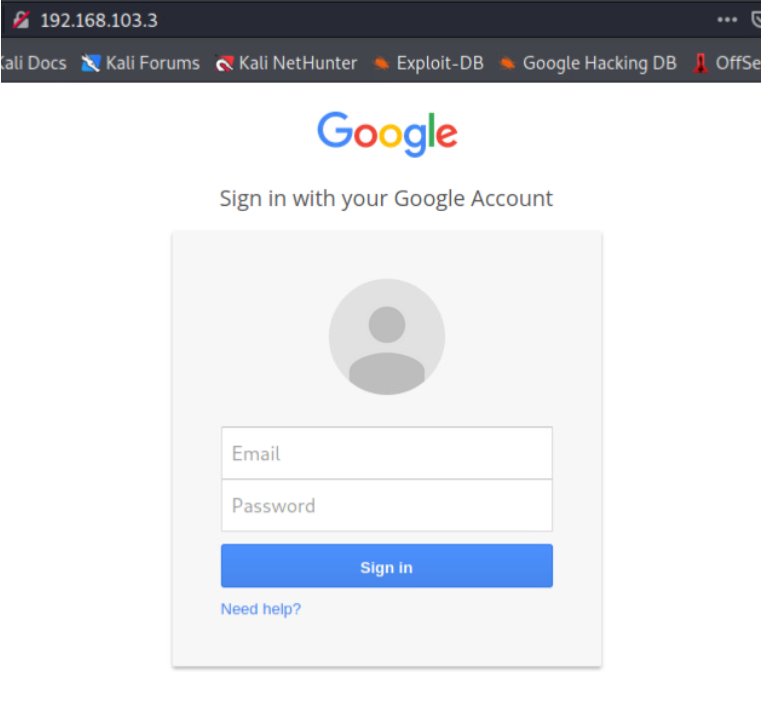
Spoofed Google sign-in
Login failed?
From there you would log in as usual by entering your username and password. As soon as you click enter not only are you not logged in, but you are also left on the same page. This webpage was fake! Once you enter your credentials, and click the “sign-in” button, the credentials will be sent directly to the attacker. The button also sends you to the actual Google Sign-in page. This leads you to believe that you may have entered your password incorrectly. But unfortunately, someone now has your login credentials.
While you were logging in…
From the attacker’s perspective, you are faced with a screen waiting for any information to be captured. Once a user submits credentials the attacker will be shown the following:
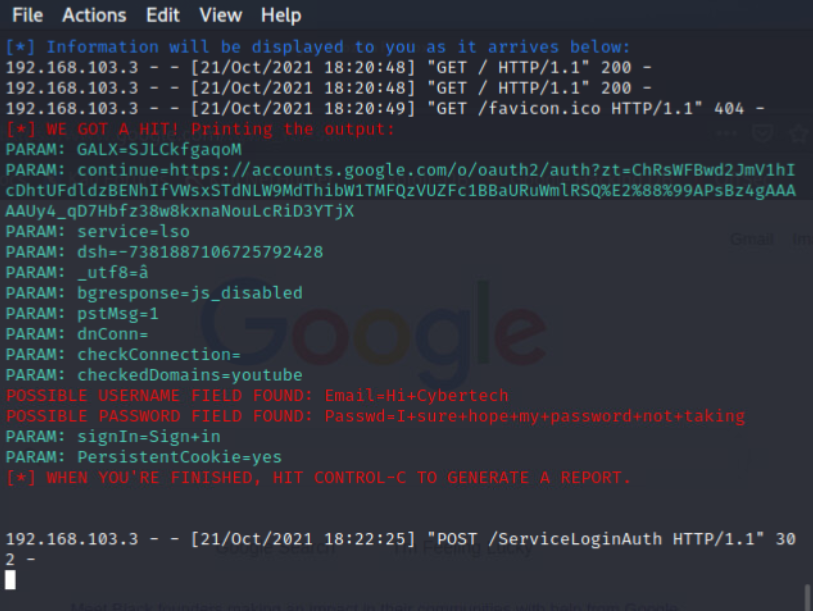
Attacker’s perspective
How Can I Prevent This?
If the Social-Engineer Toolkit can fully replicate a website, how are you able to tell if you are falling for a web credential harvest? To start, many browsers nowadays will provide a warning that the website you are about to visit is unsafe and may be dangerous. It’s never ideal to fully rely on that. When you do visit the website, take a look at the URL bar. Where there should be google.com is a set of numbers. This is known as an IP address and is the one used by the attacker to broadcast the website to the internet.
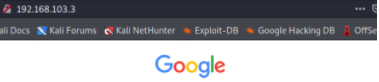
Check the URL!
2 Factor-Authentication
In the case that you do fall for this fake website and the attacker now has your login credentials, this doesn’t mean they have complete control over your account. Many platforms now provide extra methods for logging in known as 2 Factor-Authentication. 2FA is an extra method of verification when logging into accounts. This is usually done by sending a verification code to emails or phone numbers. It doesn’t have to be just one, more ways of verification can be added which is referred to as multi-factor authentication This usually involves linking an email or phone number to have a code sent whenever logging in. If the attacker does now have access to your account, then you will receive a warning to your phone or email account alerting you that someone is trying to log in. It would be wise to change your password when this happens.
Is that all the Toolkit can do?
This was just one of many different attacks that the Social Engineering Toolkit is capable of. From infecting USBs with programs or commands to sending mass spam emails to a designated list of recipients, SET can carry out various forms of attacks. In addition to this, the software is open source. Modifications can be made to the toolkit to make other types of attacks that are not currently included entirely possible.
Resources:
- “The Social-Engineer Toolkit (SET).” Open Source Tools, TrustedSec, 27 Sept. 2019, https://www.trustedsec.com/tools/the-social-engineer-toolkit-set/.
