Author: CyberTech Team
What is a wifi pineapple and why should we as internet users be aware of them? Here are some tips to make sure you aren’t falling prey to a man-in-the-middle attack!

So first, what is the web?
The web is the collection of everything and all of the data that people can find online. The internet is a way to access all of this information.
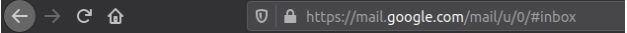
A URL (Uniform Resource Locator) is a way to locate certain bits of data on the web by writing where to find the location of the data. The URL can be broken down into different parts, but for the sake of simplicity, this entry will only break down the URL into 3 main parts:

In Image 1, the letters in red represent something called a “protocol”. This is how a user is going about to access the internet. As seen, this protocol is called HTTPS, which is the secured version of HTTP, the main way of navigating the web. The domain is in the yellow box, which is basically like the big name for the URL and everything points back to the domain. The rest that is not in boxes is the specific address to the location that is desired.
This is similar to the protocol (in red) is the means of communication (text, phone call, etc.) and the yellow is the area code to give a general idea of where to look. The rest of the number points to a specific person.
What does a WiFi Pineapple (NANO) actually do?
WiFi Pineapples mimic network routers by attaching themselves to a legitimate network (usually by just logging in), and then the WiFi Pineapple will imitate the SSID (Service Set Identifier) or network name so that people will end up connecting to the mimicked connection. This way, the users trying to connect to the internet end up connecting to a fake router that monitors traffic that passes through it.
The bare bones of the WiFi Pineapple are not as malicious, where it collects information about devices and routers but not the content that the devices may be accessing themselves. However, the great (and awful) thing about WiFi Pineapples is that they are so flexible with the many modules that the HAK5 community and fans have provided to allow the malicious actor to gain more information about the unsuspecting users.
Some of the modules are listed below in Image 2. For this blog, not every module will be covered, but some of the simple ones that enhance the abilities of the WiFi Pineapple.

WiFi Pineapples are also able to spoof any network address that the pineapple has contacted. In order to intercept the traffic, however, they need the network’s WiFi password.
So what? I mean, the devices still get internet access, right?
That is true. The devices still receive internet connection because the WiFi Pineapple was able to connect to a network before the unsuspecting users connected to it by entering in the WiFi’s password or connecting to a public network without a password. But, by doing this, the malicious actor is able to sift through a lot of information that may be passing through the WiFi Pineapple or even stored on the device connecting to it.
This is similar to phone tapping. Sure, the person on the other end is able to understand the messages that the caller is trying to convey, but someone is tapping into the middle of that conversation which the message is not intended for. This is what gives the name “Man in the Middle” Attack: a malicious actor is acting and listening in the middle of data being shared between individuals who are not supposed to have access to this information.
It does not only involve the sites that the connected devices are accessing (or the messages that the device is sending out), WiFi Pineapples also scan every network that a device has connected to previously, which is as seen in Image 3. This can be the home network at a house, a work network, the best friend’s network, and this public address that the device has just connected to.
The black boxes are all listed as a single device, and each entry is a different SSID network. The MAC address (MAC address for a device is like a device’s fingerprint, a unique identifier) column entry lists the device that was used to connect to those network SSIDs, and the SSID column entries show the names of the networks that the device has previously connected to.
While the SSID network addresses will repeat if the device has connected to the same network multiple times, the information that the WiFi Pineapple accesses is impressive and unnerving.
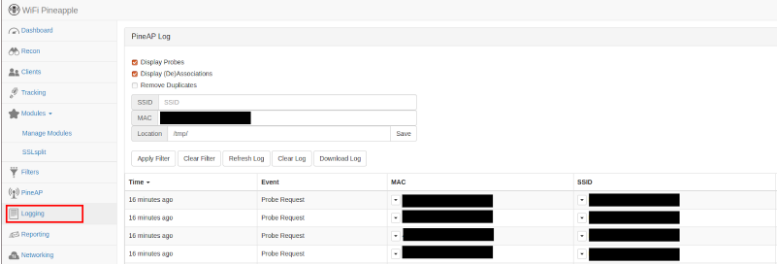
For this section, I accessed one of the tabs that are listed on the left of the screen. Under ‘modules’ attackers can easily download extra programs that can assist in collecting information. As seen below, the websites I attempted to access on my device are logged through the WiFi Pineapple that the malicious actor can easily view and parse through. This can be viewed in Image 4.
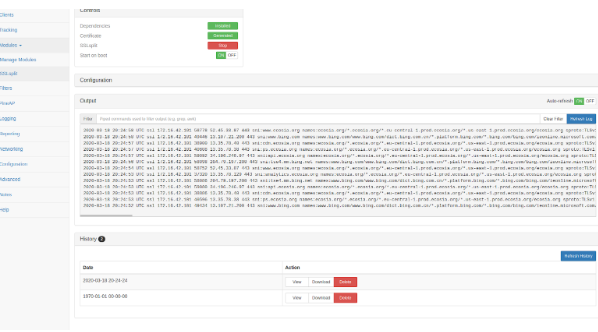
The module “DWall” on the WiFi Pineapple can mimic and read the websites that the devices connect with on the internet that is routed through it.
How can I notice if I accidentally connected to a WiFi Pineapple?
Luckily enough, many web pages reconnect their users to a more secure form of their websites using something called “HTTPS”. This can be easily spotted if an individual looks at the far left of their URL bar to spot a lock next to the website address (URL) that the individual is visiting. If the device is accidentally connected to a WiFi Pineapple, most likely the user will see the following error message in Images 5 & 6.
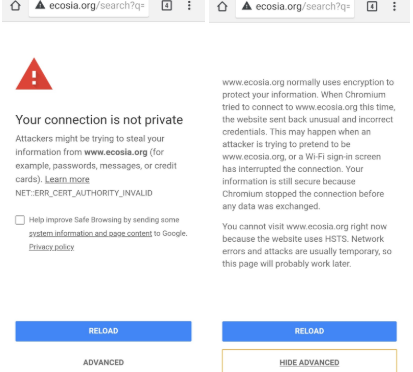
HTTP webpages, however, can still connect without a hitch even when the device is connected to a WiFi Pineapple. Image 7 illustrates this that no warnings were relayed to the user of the device that the connection may not be private.
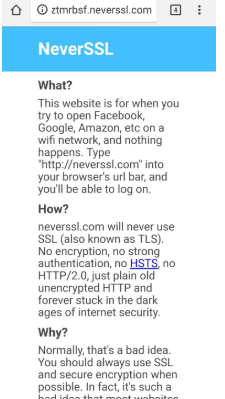
To double-check if the website is using HTTP or HTTPS, check the upper left-hand corner near the URL or website box. There should be a lock next to the URL to represent the extra layer of security that it adds.
Another more vague answer is that the internet connection will be slower. While it is very difficult to figure out whether the connection is slow because there is a WiFi Pineapple intercepting the connection or a variety of other reasons such as a heavy amount of users on the connection.
In Summary
WiFi Pineapples are a tool with different abilities, some of which can be used for a malicious attack called a Man in the Middle attack which intercepts data from devices to the internet, similarly to tapping into a phone call between two different people. Just like wiretapping (listening into phone calls), the purpose of utilizing this Man in the Middle attack is to gather information on the user.
In order to avoid such an attack, do not automatically reconnect with known WiFi networks. This may be an inconvenience, but the payoff is far greater than avoiding a couple of seconds to make sure that the WiFi network the device is connecting to is the desired one.
Another method is to be wary of public WiFis. Like previously stated, the WiFi Pineapple is able to spoof (or fake) network SSIDs; however, in order to actually intercept the web traffic, they need to enter the WiFi’s password. Public WiFis have either rather well-known passwords that are accessible to everybody or no password at all. This means that it is easy to be able to intercept traffic through the WiFi Pineapple in most public WiFi’s.
Lastly, make sure to connect to HTTPS. HTTPS adds an extra layer of security when browsing online and can provide warnings if browsing unsafely, as seen in Image 5 & 6. Image 8 is an easy way to tell if the device is connecting to a HTTPS website for that extra security.
